This lab is for the Offensive Security and Reverse Engineering course I took from OSRE instructed by Ali Hadi
We will be analyzing the provided PE file named putty.exe. The password for the archived file is infected
01. What is the magic number (Dos header) & signature (PE header) of the file?
To get the above details, we can analyze the file using CFF Explorer or PE Bear, you can use any PE analysis tool of your choice but I will go with PE-bear.
This is something you can just get by using hexdump but here is the PE-bear screenshot:

Now that we have the magic number, let's check the signature or PE header. I will still use PE-bear on this one too:

Holy shit!!.. PE-bear is such a glorious tool. We can see the PE header and the signature, very EZ right?
02. For what architecture was this file built for and which entry gave you the answer?
To get the architecture we need to look at the file header as we can see from our PE-bear screenshot:
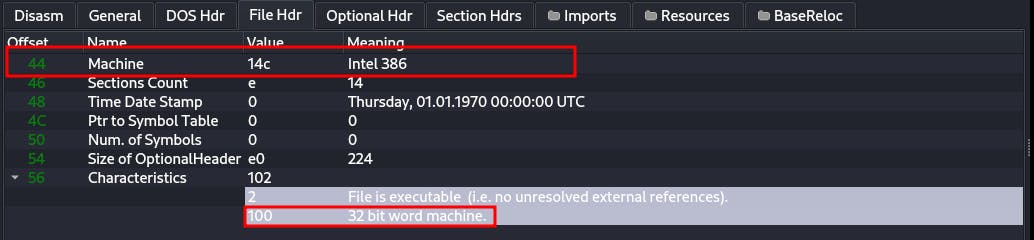
The file was built for a 32-bit architecture and the entry was from Machine with the value of Intel 386 . EZ moving on
03.What is the base address of the code section?
The base address of the code section can be found at the optional header:

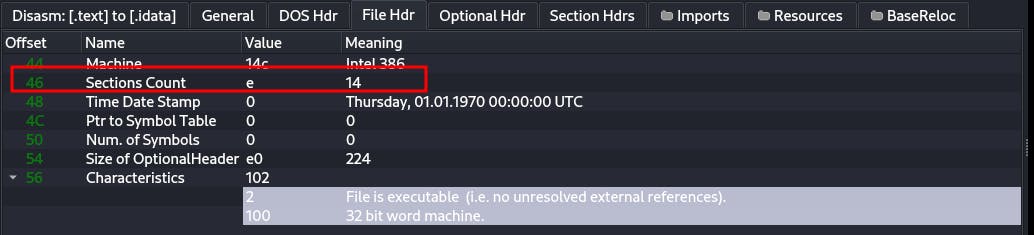
04. How many sections does this file have?
We can count manually or just check the file header to get the number of total sections:
05. What is each section used for?
This is great, each section has a specific function let's dig into all of them one by one. credits to 0xrick blog & hexacorn blog
text: Contains the executable code of the program..data: Contains the initialized data..bss: Contains uninitialized data..rdata: Contains read-only initialized data..edata: Contains the export tables..idata: Contains the import tables..reloc: Contains image relocation information..rsrc: Contains resources used by the program, these include images, icons or even embedded binaries..tls: (Thread Local Storage), provides storage for every executing thread of the program..00cfg– Control Flow Guard (CFG) section (added by newer versions of Visual Studio).xdata– Exception Information Section
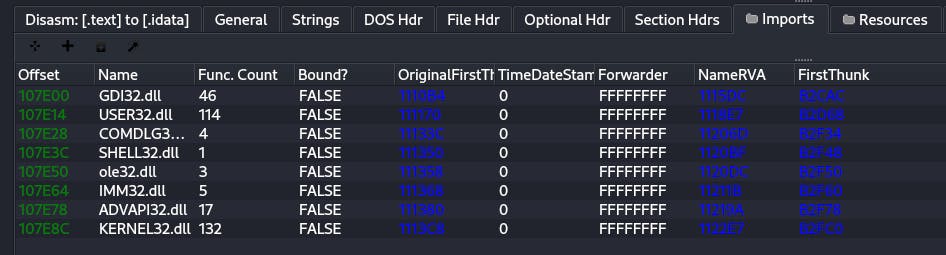
06. How many libraries is the file importing?
We can see the list of libraries imported in the Imports section
0.7 Can you change the section's flag? How?
From what I know the section flags can be edited. The process usually involves changing specific bits in the binary's header corresponding to the section's flags. However, keep in mind that modifying binary files can have unintended consequences and should be done with caution.
0.8 When was it compiled
My method of finding when was the binary compiled,is to look at the modified date in file properties

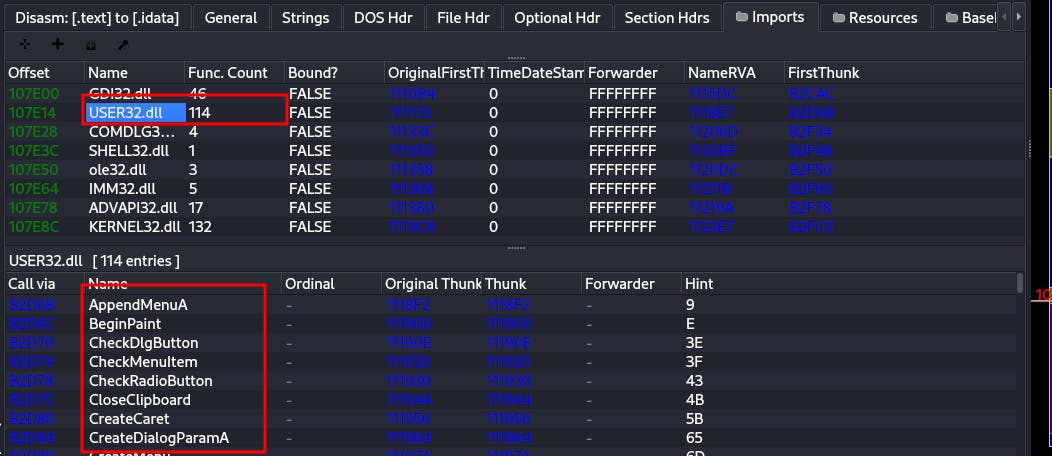
0.9 Do you know what functions are being imported
Every imported library comes with its own functions. In our case, the library USER32.dll has the following functions (114 entries):
10. Did you find the export table?
NOPE
Why do you think no table was found
The export table exists in the .edata section which happens to be missing in our binary.
12. Finally, what is the address of the entry point and what section it points?

And it points to the .text section
Conclusion
Roses are red, violets are blue, I touched grass, so should you.
Let me know if I made any mistakes in the analysis and also more information about the export table is much appreciated.
Materials
0xRick Blog (Rickest of all Ricks)
PE-Bear
OSRE YouTube playlist
(Yes I did not link them so that you can type manually and alter the google algorithm for once)
Thank you for reading my sht...GGs

